Azure for Active Directory: 7 Ultimate Power Moves for 2024
Thinking about upgrading your identity management game? Azure for Active Directory isn’t just a trend—it’s the future of secure, scalable enterprise access. Let’s dive into how it transforms the way organizations manage users, devices, and apps.
What Is Azure for Active Directory? A Modern Identity Revolution

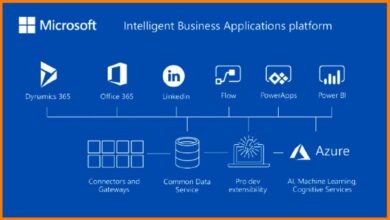
Azure for Active Directory, commonly known as Azure AD or Microsoft Entra ID (its new official name as of 2023), is Microsoft’s cloud-based identity and access management service. It enables organizations to securely manage user identities, control access to applications, and enforce conditional access policies across hybrid and cloud environments.
From On-Premises AD to Cloud Identity
Traditional Active Directory (AD) has been the backbone of enterprise identity for decades. However, with the rise of remote work, cloud applications, and mobile devices, the limitations of on-premises AD became apparent. Azure for Active Directory bridges this gap by extending identity management to the cloud.
- Legacy AD relies on domain controllers and local networks.
- Azure AD operates in the cloud, enabling global access without VPNs.
- It supports modern authentication protocols like OAuth 2.0, OpenID Connect, and SAML.
“Azure AD is not just a cloud version of Active Directory—it’s a reimagining of identity for the digital era.” — Microsoft Tech Community
Core Components of Azure for Active Directory
To understand how Azure for Active Directory works, it’s essential to break down its key components:
- Users and Groups: Centralized management of employees, partners, and external users.
- Applications: Integration with thousands of SaaS apps like Salesforce, Dropbox, and Office 365.
- Conditional Access: Policies that enforce security based on user location, device health, and sign-in risk.
- Identity Protection: AI-driven threat detection for suspicious login activities.
These components work together to provide a seamless and secure identity layer across your digital ecosystem. For more details, visit Microsoft’s official documentation.
Why Migrate to Azure for Active Directory?
Organizations are rapidly shifting from on-premises Active Directory to Azure for Active Directory due to its scalability, security, and integration capabilities. This migration is not just about moving data—it’s about transforming how identity is managed in a modern IT landscape.
Scalability and Global Reach
One of the biggest advantages of Azure for Active Directory is its ability to scale instantly. Whether you have 100 users or 100,000, Azure AD handles authentication requests globally with low latency.
- No need to manage physical domain controllers.
- Automatic replication across Microsoft’s global data centers.
- Supports multi-geography deployments with local identity caching.
This scalability makes Azure for Active Directory ideal for growing businesses and multinational corporations.
Enhanced Security and Threat Protection
Security is a top concern for IT leaders, and Azure for Active Directory delivers advanced protection features out of the box.
- Multi-Factor Authentication (MFA): Adds an extra layer of security using phone calls, SMS, or authenticator apps.
- Risk-Based Conditional Access: Blocks or challenges logins from unfamiliar locations or devices.
- Identity Protection: Uses machine learning to detect anomalies like impossible travel or leaked credentials.
According to Microsoft, organizations using Azure AD Identity Protection see a 99.9% reduction in account compromise risks. Learn more at Microsoft Security.
Key Features of Azure for Active Directory You Can’t Ignore
Azure for Active Directory isn’t just about logging in—it’s a full-featured identity platform that empowers IT teams and improves user experience.
Single Sign-On (SSO) Across Cloud and On-Premises Apps
SSO is one of the most loved features of Azure for Active Directory. Users can access all their apps—whether in the cloud or on-premises—with a single set of credentials.
- Supports over 2,600 pre-integrated SaaS applications.
- Enables seamless access to on-premises apps via Azure AD Application Proxy.
- Reduces password fatigue and improves productivity.
For example, a user can log in once and access Office 365, Salesforce, and an internal HR portal without re-entering credentials.
Conditional Access: Smart Policies for Smarter Security
Conditional Access allows organizations to define rules that control how and when users can access resources.
- Require MFA for high-risk sign-ins.
- Block access from unmanaged devices.
- Enforce compliance with Intune-managed devices.
These policies are dynamic and adapt to real-time risk assessments. For instance, if a user logs in from Nigeria but usually works from Canada, Azure AD can prompt for additional verification.
Self-Service Password Reset and User Management
Empowering users to manage their own accounts reduces helpdesk workload and improves efficiency.
- Users can reset passwords without calling IT.
- Managers can approve access requests via the MyAccess portal.
- Guest users can be invited and managed easily for collaboration.
This self-service capability is a game-changer for large organizations with distributed teams.
Hybrid Identity: Bridging On-Premises and Cloud with Azure for Active Directory
Most enterprises don’t operate in a purely cloud or on-premises environment—they need both. Azure for Active Directory supports hybrid identity scenarios through tools like Azure AD Connect.
What Is Azure AD Connect?
Azure AD Connect is a synchronization tool that links your on-premises Active Directory with Azure for Active Directory.
- Syncs user accounts, groups, and passwords in real time.
- Supports password hash synchronization, pass-through authentication, and federation.
- Enables seamless single sign-on for hybrid users.
It ensures that users have a consistent identity across both environments, reducing confusion and improving security.
Password Hash Sync vs. Pass-Through Authentication
When setting up hybrid identity, organizations must choose how authentication is handled.
- Password Hash Sync (PHS): Stores a hash of on-premises passwords in Azure AD. Users can sign in even if on-premises servers are down.
- Pass-Through Authentication (PTA): Validates credentials against on-premises AD in real time. More secure but requires on-premises agents.
Microsoft recommends PTA for better security, but PHS offers higher availability. The choice depends on your organization’s risk tolerance and infrastructure.
Federation with AD FS
For organizations with existing AD FS (Active Directory Federation Services) infrastructure, Azure for Active Directory supports federation.
- Enables SSO using SAML or WS-Fed protocols.
- Useful for legacy applications that require federation.
- Can be migrated to PTA over time for simplified management.
However, Microsoft encourages moving away from AD FS to Azure AD’s native authentication methods for better reliability and lower TCO.
Managing External Users with Azure for Active Directory B2B
Collaboration doesn’t stop at company boundaries. Azure for Active Directory B2B (Business-to-Business) allows secure sharing with partners, vendors, and contractors.
How Azure AD B2B Works
With Azure AD B2B, you can invite external users to access your applications and resources.
- Guest users receive an email invitation and sign in with their own work or personal accounts.
- Access is controlled via groups and conditional access policies.
- Admins can monitor guest activity and revoke access anytime.
This eliminates the need to create separate local accounts for every external collaborator.
Access Reviews and Governance
Security doesn’t end at granting access—it continues with ongoing governance.
- Set up automated access reviews to ensure guest accounts aren’t overprivileged.
- Define expiration policies for temporary collaborations.
- Integrate with Azure AD Privileged Identity Management (PIM) for just-in-time access.
These features help maintain compliance with regulations like GDPR, HIPAA, and SOX.
Seamless Collaboration with Microsoft 365
Azure for Active Directory B2B integrates tightly with Microsoft 365 apps like Teams, SharePoint, and OneDrive.
- External users can join Teams meetings and collaborate on documents.
- SharePoint sites can be shared with guests while maintaining version control.
- All collaboration is logged and auditable.
This makes Azure AD B2B a powerful tool for modern, interconnected business ecosystems.
Securing Identities with Azure for Active Directory Identity Protection
In today’s threat landscape, proactive security is non-negotiable. Azure for Active Directory Identity Protection uses AI and machine learning to detect and respond to identity-based threats.
Detecting Risky Sign-Ins
Identity Protection continuously monitors sign-in activities for signs of compromise.
- Flags sign-ins from anonymous IPs (e.g., Tor networks).
- Detects impossible travel (e.g., logging in from two countries in one hour).
- Identifies sign-ins from infected devices.
Each risky sign-in is assigned a risk level—low, medium, or high—allowing admins to respond appropriately.
User Risk vs. Sign-In Risk
Azure AD distinguishes between two types of risk:
- User Risk: Based on user behavior anomalies, like leaked credentials found on the dark web.
- Sign-In Risk: Based on the context of a specific login attempt, such as unfamiliar location or device.
Conditional Access policies can be configured to respond to either or both types of risk, enabling granular control.
Automated Remediation with Risk-Based Policies
Instead of manually investigating every alert, Azure for Active Directory allows automated responses.
- Require MFA for medium-risk sign-ins.
- Block access for high-risk attempts.
- Force password reset for compromised user accounts.
This automation reduces response time and minimizes the impact of potential breaches.
Best Practices for Implementing Azure for Active Directory
Deploying Azure for Active Directory successfully requires planning, governance, and ongoing management.
Start with a Clear Identity Strategy
Before deploying Azure for Active Directory, define your identity goals.
- Are you going all-cloud or maintaining hybrid?
- What applications need SSO?
- How will you manage guest access?
A clear strategy ensures alignment across IT, security, and business units.
Enable Multi-Factor Authentication for All Users
MFA is the single most effective way to prevent unauthorized access.
- Enforce MFA for admins first, then expand to all users.
- Use the Microsoft Authenticator app for passwordless authentication.
- Consider phishing-resistant methods like FIDO2 security keys.
Microsoft reports that MFA blocks over 99.9% of account compromise attacks.
Use Role-Based Access Control (RBAC)
Assign permissions based on job roles, not individuals.
- Create custom roles for granular control.
- Avoid assigning global admin privileges unnecessarily.
- Regularly review role assignments for least privilege.
RBAC reduces the risk of insider threats and accidental misconfigurations.
Monitor and Audit with Azure AD Logs
Visibility is key to security and compliance.
- Use the Azure AD audit log to track user and admin activities.
- Set up alerts for critical events like admin role changes.
- Integrate with Microsoft Sentinel for advanced threat hunting.
Regular audits help detect anomalies and demonstrate compliance during audits.
Common Challenges and How to Overcome Them
While Azure for Active Directory offers immense benefits, organizations often face challenges during adoption.
Legacy Application Compatibility
Not all applications support modern authentication protocols.
- Solution: Use Azure AD Application Proxy to publish on-premises apps securely.
- Modernize legacy apps over time with API wrappers or migration plans.
- Leverage service principals for non-interactive app access.
Gradual modernization ensures business continuity while improving security.
User Resistance to Change
Employees may resist new login processes or MFA prompts.
- Solution: Provide clear communication and training.
- Highlight benefits like reduced password resets and better security.
- Use phased rollouts to minimize disruption.
Change management is as important as technical implementation.
Complex Licensing and Cost Management
Azure AD has multiple licensing tiers (Free, Office 365, P1, P2), which can be confusing.
- Solution: Audit your requirements and choose the right tier.
- P1 includes Conditional Access and Identity Protection basics.
- P2 adds advanced Identity Protection, Access Reviews, and PIM.
Use Azure Cost Management to track and optimize spending.
What is Azure for Active Directory?
Azure for Active Directory (Azure AD), now known as Microsoft Entra ID, is a cloud-based identity and access management service that helps organizations manage user identities, secure access to applications, and enforce conditional access policies across hybrid and cloud environments.
How does Azure AD differ from on-premises Active Directory?
On-premises Active Directory is designed for local network authentication using domain controllers, while Azure for Active Directory is cloud-native, supports modern authentication protocols (OAuth, OpenID Connect), and enables global access without requiring a VPN. It also includes advanced security features like Identity Protection and Conditional Access.
Can Azure AD replace on-premises Active Directory?
While Azure AD can handle many identity tasks, most enterprises use a hybrid model. Azure AD extends on-premises AD through synchronization tools like Azure AD Connect. Full replacement is possible for cloud-only organizations, but legacy systems often require on-premises AD.
What is the cost of using Azure for Active Directory?
Azure AD has a Free tier with basic features. Paid tiers include P1 ($6/user/month) and P2 ($9/user/month), offering advanced security and governance. Licensing is often bundled with Microsoft 365 subscriptions.
How do I get started with Azure for Active Directory?
Start by creating an Azure AD tenant in the Azure portal. Then, sync your on-premises AD using Azure AD Connect, enable MFA, configure SSO for key apps, and set up Conditional Access policies. Microsoft provides step-by-step guides at learn.microsoft.com.
Adopting Azure for Active Directory is more than a technical upgrade—it’s a strategic move toward a secure, scalable, and user-friendly identity foundation. From hybrid environments to external collaboration and AI-driven threat detection, Azure for Active Directory empowers organizations to thrive in the digital age. By following best practices and leveraging its full suite of features, businesses can achieve seamless access, robust security, and compliance with ease.
Recommended for you 👇
Further Reading: